Enhanced Cybersecurity Feature Takes Effect for Students

Stetson University will launch an additional layer of online security known as multi-factor authentication this month for students, faculty and staff to log in when they are off-campus.
Stetson will be a pioneer in cybersecurity initiatives as it is the first higher-education institution in the country to develop its own multi-factor authentication for its online services. The multi-factor authentication process will require students, faculty and staff to verify their identity in two ways when they log in from an off-campus location.
For example, users will need their password and a numeric code texted to their mobile phone. The Stetson multi-factor authentication will offer the added flexibility to use biometrics, such as a fingerprint or facial recognition, to confirm one’s identity in addition to other options, such as passwords, tokens, text messages and push notifications.
The new security feature will go live on Stetson’s four campuses in DeLand, Celebration, Gulfport and Tampa on:
- Monday, Jan. 20, for non-faculty employees
- Monday, Feb. 3, for faculty
- Monday, March 9, for students
How to use Multi-Factor Authentication?

Users will be required to complete an extra step (typically on their mobile phones) after they enter their User ID and Password to log in while they are off campus. Users will be required to use two authenticators and will be prompted to download these to their mobile device when they log in:
• Stetson Authenticator – for all Stetson services, such as myStetson, Banner and Blackboard

• Microsoft Authenticator – for all Microsoft services, such as Outlook email, Office 365, OneDrive, etc.
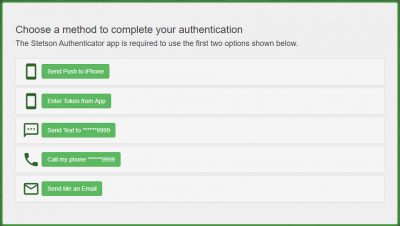
There are five main options for these authenticator apps:
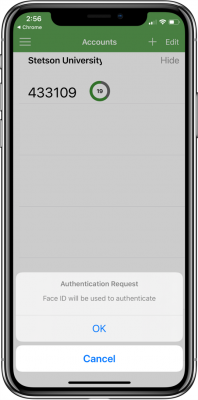
A. Users receive a notification on their mobile devices via the Authenticator app. They can then accept or decline it.
B. Users read a one-time-use token from the Authenticator app and enter it on the screen provided.
C. Users receive a one-time-use token via text message on their registered phones and enter it on the screen provided.
D. Users receive a phone call on their registered phones and respond to it using the prompts.
E. Users receive a one-time-use token via a non-Stetson email that they will indicate during sign up. They will then need to enter it on the screen provided (This option is only available for Stetson Authenticator).
Although the multi-factor authentication is designed by default to be used off-campus, users have the option to choose to use it on-campus, as well. They will need to indicate their preferences during registration or subsequently through their settings page on the MyStetson portal. Certain users with access to confidential and sensitive information like Banner administrative users and IT users will be required to use this security feature irrespective of their location.
Users will also have the option to trust their frequently used browsers, so that they will not be prompted to use multi-factor authentication for 30 days while using those browsers.
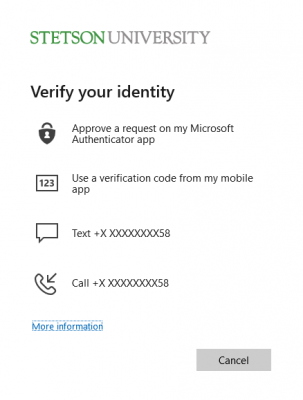
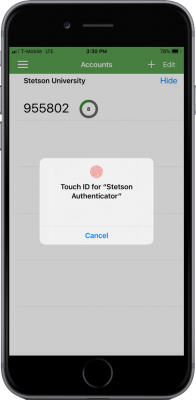
In addition, since the Stetson Authenticator mobile app has biometric authentication capabilities, users can use their phone’s TouchID or FaceID (fingerprint and face recognition capabilities), if applicable, while responding to the notifications received (Select Option A above: “Send Push to Phone”).
Go-Live dates for Multi-Factor Authentication
Starting in fall 2019, both the Stetson and Microsoft multi-factor authentication systems were tested on a pilot basis by users in IT and by students in a Management Information Systems (MIS) class, taught by Vikram Ahmed, EdD, director of Stetson’s Enterprise Information Systems (EIS).
The first group to go live was Banner administrative users on Nov. 4. The security feature will be launched to the three remaining groups of users on all Stetson campuses starting Monday, Jan. 20, for all non-faculty employees; Monday, Feb. 3, for all faculty; and Monday, March 9, for all students.
When users log in on or after the go-live date for their respective group, they will receive a prompt to download the Stetson Authenticator Mobile App and the Microsoft Authenticator Mobile App (available on Apple App Store and Google Play) on their iOS or Android phone, set up their preferences (including phone numbers to receive text messages and calls, and an external non-Stetson email address for the Stetson multi-factor authentication); and follow the instructions to complete the login.
They also have the option to enroll to use this feature before the respective go-live dates. The link: https://my.stetson.edu/apps/mfainfo/ has all the details and instructions.
IT will continue to send updates as the launch dates approach, as well as dates for trainings and demonstrations. For any questions or concerns, please contact I.T. at [email protected].
The approved policy for use of multi-factor authentication to access Stetson’s network can be found at: https://www.stetson.edu/administration/information-technology/media/IT%20Policy%20-%20Network%20Security%20Policy.pdf
The Basics of Multi-Factor Authentication
One of the first steps of cybersecurity is access control, which involves the identification and authentication of users. There are three common factors used for authentication:
- Something users know (such as their passwords)
- Something users have (such as their mobile phones)
- Something users are (such as their fingerprints or face recognitions)

Identification occurs when users indicate their identity (such as with a username), and authentication occurs when users prove their identity. For example, users are authenticated when they provide both their username and their correct password. Permissions, rights and privileges are then granted to users based on their proven identities. Among the three authentication factors indicated above, passwords are the most commonly used, but are also the least secure. As Verizon’s 2018 Data Breach Investigations Report noted, “Eighty-one percent of hacking-related security breaches leveraged stolen and/or weak passwords.”
Multi-factor authentication is a method in which a user is granted access only after successfully presenting two or more of the above factors for authentication. For example, users may enter a password (something they know) and respond to a notification on their phone (something they have) to complete the login process. The idea behind this approach is the understanding that a perpetrator may somehow obtain a user’s password, but is very unlikely to have access to the user’s phone as well. Thus, the security of the authentication process is enhanced.
Multi-Factor Authentication at Stetson University
Over the past 18 months, the Stetson Information Technology (IT) department has been researching Multi-Factor Authentication solutions to increase security, as well as to address IT security audit suggestions.
After the research was completed, the department received proposals from a couple of vendors of multi-factor authentication solutions that included an annual price in the range of $25,000-$30,000 to cover all of the university users. Additional research showed that a common practice in academia is to separate Microsoft products (email, OneDrive, Office365, etc.) from the institution’s enterprise systems.
For Stetson, those systems include Banner, MyStetson, Blackboard, Slate and many others. Following this design, the IT department took advantage of the university’s existing Microsoft License to deploy Microsoft multi-factor authentication for the Microsoft products at no additional cost to Stetson.
At the same time, the Enterprise Information Systems (EIS) unit of IT developed a multi-factor authentication system using internal resources. This solution known as Stetson multi-factor authentication has been designed to be used with the university’s enterprise systems.
Stetson’s multi-factor authentication comes with a mobile app that has been tested and validated by both Apple and Android prior to being included in their respective app stores. In addition, this Stetson Authenticator app advances the security component by incorporating biometrics (fingerprint, face recognition) as an authentication factor.
Ahmed, director of Enterprise Information Systems, said, “Effective cybersecurity is a balance between convenience and security for the user. Stetson MFA combines the best of these two diametrically opposite goals to create an efficient, convenient and secure solution. Very few (if any) MFA commercial solutions offer the use of biometrics as a standard option, and the fact that this solution was completely developed in-house underlines the quality of talent available in EIS.
“In addition, since this solution has been built in-house, we have the flexibility to make required changes quickly and easily, something that would not be available with a commercial solution,” he added.
Matthew Samuels, Applications analyst/developer in EIS and the chief architect of the Stetson Multi-Factor Authentication system, shared his experiences working on this solution, “Developing Stetson MFA was a massive, ambitious project involving many different technologies, such as our single sign-on system (CAS), cloud services in Amazon Web Services (AWS), and various software frameworks.
“After quite a bit of research and development, our year-long endeavor has culminated in a system that provides a variety of methods to finish logging in using MFA and provide an extra layer of security to the Stetson community,” he added.



